This page explains states and a typical flow of client-managed secret mode with the did:ebsi method. See https://identity.foundation/did-registration/#client-managed-secret-mode for more information about the protocol.
¶ States
Possible states:
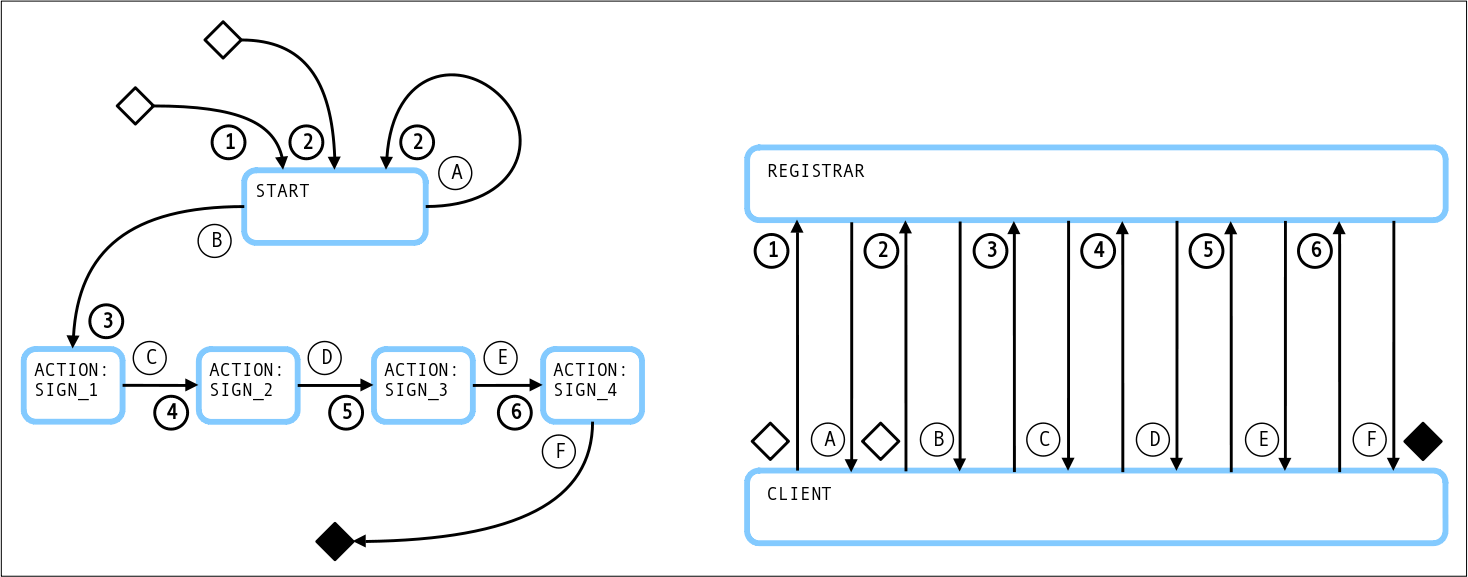
¶ Requests and Responses
¶ Request 1: Missing verificationMethod "#key-1"
Supported secrets:
- VerifiableAuthorisationToOnboard: An onboarding token called "VerifiableAuthorisationToOnboard" from an EBSI onboarding seervice is required to register an DID in to EBSI network.
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/create?method=ebsi" \
-H "Content-Type: application/json" \
-d '{
"options": {
"clientSecretMode": true
},
"secret": {
"VerifiableAuthorisationToOnboard": "eyJhbGciOiJFUzI1NiIsImtpZCI6ImRpZDplYnNpOnpqVW5FeHN5eXdlUTlwNGN5M252clZjI2l5Z1VZZURYM0ZvSklSTzdzWmI5bXN2enRxVmZJVU5rZFpwWlA1MmoxLUkiLCJ0eXAiOiJKV1QifQ.eyJleHAiOjE3NDMzNDg5NDAsImlhdCI6MTc0MjQ4NDk0MCwiaXNzIjoiZGlkOmVic2k6empVbkV4c3l5d2VROXA0Y3kzbnZyVmMiLCJqdGkiOiJ2YzplYnNpOmNvbmZvcm1hbmNlI2E2MWY4ODhhLWRmMTctNDI2Yi04Njg2LTA1NTQ5MDdlZTE2ZiIsIm5iZiI6MTc0MjQ4NDk0MCwic3ViIjoiZGlkOmVic2k6enVIZWJ2R3NKV0J0akpCNjVaeUhjRDgiLCJ2YyI6eyJAY29udGV4dCI6WyJodHRwczovL3d3dy53My5vcmcvMjAxOC9jcmVkZW50aWFscy92MSJdLCJjcmVkZW50aWFsU2NoZW1hIjp7ImlkIjoiaHR0cHM6Ly9hcGktcGlsb3QuZWJzaS5ldS90cnVzdGVkLXNjaGVtYXMtcmVnaXN0cnkvdjMvc2NoZW1hcy96M01nVUZVa2I3MjJ1cTR4M2R2NXlBSm1uTm16REZlSzVVQzh4ODNRb2VMSk0iLCJ0eXBlIjoiRnVsbEpzb25TY2hlbWFWYWxpZGF0b3IyMDIxIn0sImNyZWRlbnRpYWxTdWJqZWN0Ijp7ImlkIjoiZGlkOmVic2k6enVIZWJ2R3NKV0J0akpCNjVaeUhjRDgifSwiZXhwaXJhdGlvbkRhdGUiOiIyMDI1LTAzLTMwVDE1OjM1OjQwLjAwMFoiLCJpZCI6InZjOmVic2k6Y29uZm9ybWFuY2UjYTYxZjg4OGEtZGYxNy00MjZiLTg2ODYtMDU1NDkwN2VlMTZmIiwiaXNzdWFuY2VEYXRlIjoiMjAyNS0wMy0yMFQxNTozNTo0MC4wMDBaIiwiaXNzdWVkIjoiMjAyNS0wMy0yMFQxNTozNTo0MC4wMDBaIiwiaXNzdWVyIjoiZGlkOmVic2k6empVbkV4c3l5d2VROXA0Y3kzbnZyVmMiLCJ0ZXJtc09mVXNlIjp7ImlkIjoiaHR0cHM6Ly9hcGktcGlsb3QuZWJzaS5ldS90cnVzdGVkLWlzc3VlcnMtcmVnaXN0cnkvdjUvaXNzdWVycy9kaWQ6ZWJzaTp6alVuRXhzeXl3ZVE5cDRjeTNudnJWYy9hdHRyaWJ1dGVzLzlhYjQzNGNhZmIzYjMzMjc5NDFmOTQyMmU4OGVmZDkzYzZjZmY5ZGRhNjc4ZjhhYTQ3ZmRjMjM4ZjhiZWMzY2UiLCJ0eXBlIjoiSXNzdWFuY2VDZXJ0aWZpY2F0ZSJ9LCJ0eXBlIjpbIlZlcmlmaWFibGVDcmVkZW50aWFsIiwiVmVyaWZpYWJsZUF0dGVzdGF0aW9uIiwiVmVyaWZpYWJsZUF1dGhvcmlzYXRpb25Ub09uYm9hcmQiXSwidmFsaWRGcm9tIjoiMjAyNS0wMy0yMFQxNTozNTo0MC4wMDBaIn19.GzGiQpSBS5ZUQ06Z91MHzZQYXNDsUqzHCXGh31QKLzn5RtmpfFd3CgldE1QvwrNjOLzTrWqFzLXEPCgmJQY_aw"
},
"didDocument": {
"@context": ["https//www.w3.org/ns/did/v1"],
"service": [{
"id": "#didcomm",
"type": "DIDComm",
"serviceEndpoint": "https://test.com/mydidcomm/endpoint"
}]
}
}'
¶ Response A: action=getVerificationMethod
{
"jobId": null,
"didState": {
"state": "action",
"action": "getVerificationMethod",
"verificationMethodTemplate": [{
"id": "#key-1",
"type": "EcdsaSecp256k1VerificationKey2019"
}],
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}
¶ Request 2: verificationMethod "#key-1"
Supported secrets:
- token: A token from an EBSI onboarding service, can be obtained here: https://app-pilot.ebsi.eu/users-onboarding/v2
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/create?method=ebsi" \
-H "Content-Type: application/json" \
-d '{
"options": {
"clientSecretMode": true
},
"secret": {
"VerifiableAuthorisationToOnboard": "eyJhbGciOiJFUzI1NksiLCJ0eXAiOiJ..."
},
"didDocument": {
"@context": ["https//www.w3.org/ns/did/v1"],
"verificationMethod": [{
"id": "#key-1",
"type": "EcdsaSecp256k1VerificationKey2019",
"publicKeyHex": "<-- hex encoded -->"
}],
"service": [{
"id": "#didcomm",
"type": "DIDComm",
"serviceEndpoint": "https://test.com/mydidcomm/endpoint"
}]
}
}'
¶ Responses B and C and D: action=signPayload with "signingRequest1"
{
"jobId": "00000000-0000-0000-0000-000000000000",
"didState": {
"state": "action",
"action": "signPayload",
"signingRequest": {
"signingRequest1": {
"kid": "#key-1",
"alg": "ES256K",
"payload": { ... },
"serializedPayload": "<-- base 64 encoded -->"
}
}
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}
¶ Requests 3 and 4 and 5: signingResponse for "signingRequest1"
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/create?method=ebsi" \
-H "Content-Type: application/json" \
-d '{
"jobId": "00000000-0000-0000-0000-000000000000",
"options": {
"clientSecretMode": true
},
"secret": {
"signingResponse": {
"signingRequest1": {
"signature": "<-- base64 encoded -->"
}
}
},
"didDocument": { }
}'
¶ Response E: action=signPayload with "signingRequest1"
{
"jobId": "00000000-0000-0000-0000-000000000000",
"didState": {
"state": "action",
"action": "signPayload",
"signingRequest": {
"signingRequest1": {
"kid": "#key-1",
"alg": "ES256KCC",
"payload": { ... },
"serializedPayload": "<-- base 64 encoded -->"
}
}
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}
¶ Request 6: signingResponse for "signingRequest1"
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/create?method=ebsi" \
-H "Content-Type: application/json" \
-d '{
"jobId": "00000000-0000-0000-0000-000000000000",
"options": {
"clientSecretMode": true
},
"secret": {
"signingResponse": {
"signingRequest1": {
"signature": "<-- base64 encoded -->"
}
}
},
"didDocument": { }
}'
¶ Response F: state=finished
{
"jobId": "00000000-0000-0000-0000-000000000000",
"didState": {
"state": "finished",
"did": "did:ebsi:zqSjfbi9GYR6cHuehD85ePw",
"secret": { }
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}
¶ OpenSSL Commands
¶ For Request 2:
Generate a new DID controller keypair (secp256k1):
openssl ecparam -genkey -name secp256k1 -outform DER >privkey
openssl ec -conv_form uncompressed -in privkey -pubout -out pubkey -inform DER -outform DER
Convert DID controller public key to hex:
cat pubkey| tail -c +24| basenc -w0 --base16
The result can then be used as value of publicKeyHex in Request 2.
¶ For Response B or C or D or E:
Extract the value of serializedPayload from Response B or Response C or Response D or Response E. Then Base64-decode the payload and write to a file:
echo "<-- base64 encoded -->"| basenc -d --base64 >payload
¶ For Requests 3 or 4 or 5:
Sign the payload with the DID controller private key:
openssl pkeyutl -sign -rawin -in payload -inkey privkey -keyform DER -digest sha256 >signature_der
openssl asn1parse -in signature_der -inform DER| sed 2!d| cut -d ':' -f4| basenc -d --base16 >signature_bin
openssl asn1parse -in signature_der -inform DER| sed 3!d| cut -d ':' -f4| basenc -d --base16 >>signature_bin
cat signature_bin| basenc -w0 --base64 >signature
The result can then be used as value of signature in Request 3 or Request 4 or Request 5.
¶ For Requests 6:
Sign the payload with the DID controller private key:
openssl pkeyutl -sign -rawin -in payload -inkey privkey -keyform DER -digest sha3-256 >signature_der
openssl asn1parse -in signature_der -inform DER| sed 2!d| cut -d ':' -f4| basenc -d --base16 >signature_bin
openssl asn1parse -in signature_der -inform DER| sed 3!d| cut -d ':' -f4| basenc -d --base16 >>signature_bin
cat signature_bin| basenc -w0 --base64 >signature
The result can then be used as value of signature in Request 6.