This page explains states and a typical flow of client-managed secret mode with the did:ethr method. See https://identity.foundation/did-registration/#client-managed-secret-mode for more information about the protocol.
¶ States
Possible states:
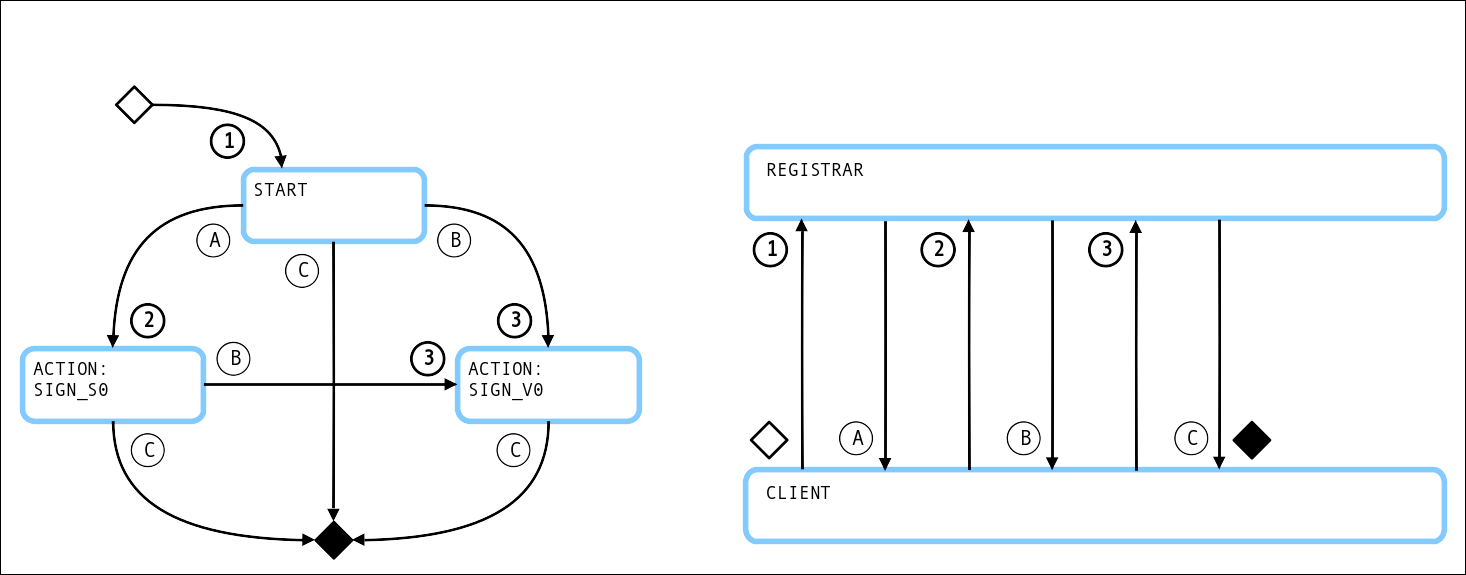
¶ Requests and Responses
¶ Request 1:
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/update?method=ethr" \
-H "Content-Type: application/json" \
-d '{
"did": "did:ethr:goerli:0x026b58dd4993fcd039c7f77dbef1b5c8b1c9ceaeccdd891b22def15b5e5ba0804d",
"options": {
"clientSecretMode": true
},
"secret": { },
"didDocumentOperation": "addToDidDocument",
"didDocument": {
"service": [{
"id": "did:ethr:goerli:0x026b58dd4993fcd039c7f77dbef1b5c8b1c9ceaeccdd891b22def15b5e5ba0804d#service-1",
"type": "DIDCommMessaging",
"serviceEndpoint": "http://localhost:8080/messaging"
}]
}
}'
¶ Response A: action=signPayload with "signingRequestS0"
{
"jobId": null,
"didState": {
"state": "action",
"action": "signPayload",
"signingRequest": {
"signingRequestS0": {
"kid": "did:ethr:goerli:0x03f1fbd3a9e4af11e605c7d0be18a66df12837b1c94a820572fbab5a4fd9167f7b#controllerKey",
"alg": "ES256KRR",
"serializedPayload": "<-- base 64 encoded -->"
}
}
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}
¶ Request 2: signingResponse for "signingRequestS0"
curl -H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-X POST "https://api.godiddy.com/0.1.0/universal-registrar/update?method=ethr" \
-H "Content-Type: application/json" \
-d '{
"did": "did:ethr:goerli:0x03f1fbd3a9e4af11e605c7d0be18a66df12837b1c94a820572fbab5a4fd9167f7b",
"options": {
"clientSecretMode": true
},
"secret": {
"signingResponse": {
"signingRequestS0": {
"signature": "<-- base64 encoded -->"
}
}
},
"didDocumentOperation": "addToDidDocument",
"didDocument": {
"service": [{
"id": "did:ethr:goerli:0x03f1fbd3a9e4af11e605c7d0be18a66df12837b1c94a820572fbab5a4fd9167f7b#service-1",
"type": "DIDCommMessaging",
"serviceEndpoint": "http://localhost:8080/messaging"
}]
}
}'
¶ OpenSSL Commands
¶ For Response A:
Extract the value of serializedPayload from Response A. Then Base64-decode the payload and write to a file:
echo "<-- base64 encoded -->"|basenc -d --base64 >payload
¶ For Request 2:
Sign the payload with the DID controller private key:
openssl pkeyutl -sign -in payload -inkey privkey -keyform DER >signature_der
openssl asn1parse -in signature_der -inform DER| sed 2!d| cut -d ':' -f4| basenc -d --base16 >signature_bin
openssl asn1parse -in signature_der -inform DER| sed 3!d| cut -d ':' -f4| basenc -d --base16 >>signature_bin
echo -n "1B"| basenc -d --base16 >>signature_bin # or 1C instead of 1B (recovery bit)
cat signature_bin| basenc -w0 --base64 >signature
The result can then be used as value of signature in Request 2.