Appearance
did:key Create
This page explains states and a typical flow of client-managed secret mode with the did:key method.
States
Possible states:
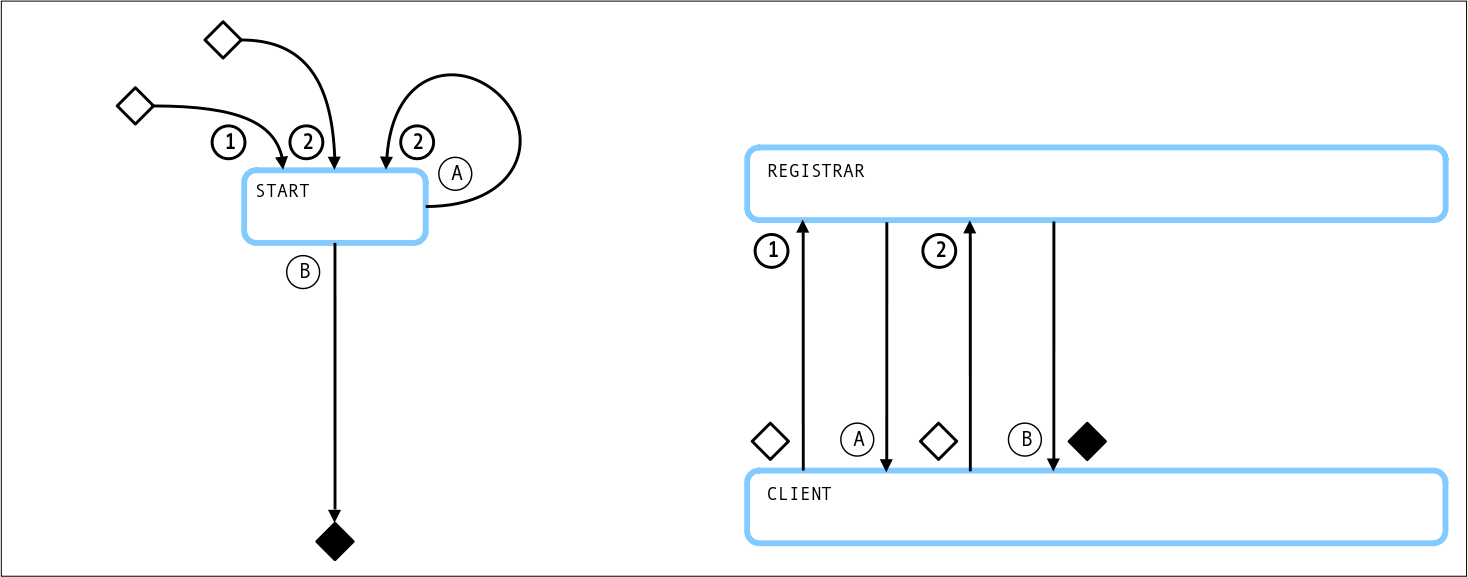
Requests and Responses
Request 1: Missing verificationMethod "#temp"
Supported options:
keyType: The type of key to create (possible values:Ed25519,secp256k1,P-256)
bash
curl -X POST "https://api.godiddy.com/1.0.0/universal-registrar/create?method=key" \
-H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-H "Content-Type: application/json" \
-d '{
"options": {
"clientSecretMode": true,
"keyType": "Ed25519"
},
"secret": { },
"didDocument": { }
}'1
2
3
4
5
6
7
8
9
10
11
2
3
4
5
6
7
8
9
10
11
Response A: action=getVerificationMethod
json
{
"jobId": null,
"didState": {
"state": "action",
"action": "getVerificationMethod",
"verificationMethodTemplate": [{
"id": "#temp",
"type": "JsonWebKey2020",
"purpose": ["authentication"],
"publicKeyJwk": {
"kty": "OKP",
"crv": "Ed25519"
}
}]
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
Request 2: verificationMethod "#temp"
bash
curl -X POST "https://api.godiddy.com/1.0.0/universal-registrar/create?method=key" \
-H "Authorization: Bearer b082c420-df67-4b06-899c-b7c51d75fba0" \
-H "Content-Type: application/json" \
-d '{
"options": {
"clientSecretMode": true
},
"secret": { },
"didDocument": {
"@context": ["https//www.w3.org/ns/did/v1"],
"verificationMethod": [{
"id": "#temp",
"type": "JsonWebKey2020",
"publicKeyJwk": {
"kty": "OKP",
"crv": "Ed25519",
"x": "a0xf_YWRIGbPri6DjBygvDKvu4ddhNlBA5wetM2CHnk"
}
}]
}
}'1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
Response B: state=finished
json
{
"jobId": "00000000-0000-0000-0000-000000000000",
"didState": {
"state": "finished",
"did": "did:key:z6Mkmg7DTLp6C6utxFduNBPvVohuHgVomCHV7YBH4suxRfwv",
"secret": {
"verificationMethod": [
[{
"id": "#temp",
"purpose": ["authentication"]
}, {
"id": "did:key:z6Mkmg7DTLp6C6utxFduNBPvVohuHgVomCHV7YBH4suxRfwv#z6Mkmg7DTLp6C6utxFduNBPvVohuHgVomCHV7YBH4suxRfwv",
"controller": "did:key:z6Mkmg7DTLp6C6utxFduNBPvVohuHgVomCHV7YBH4suxRfwv",
"purpose": ["authentication", "assertionMethod", "capabilityInvocation", "capabilityDelegation", "keyAgreement"]
}]
]
}
},
"didRegistrationMetadata": { ... },
"didDocumentMetadata": { ... }
}1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
OpenSSL Commands
For Request 2
See Request 2.
Generate a new DID controller keypair (Ed25519):
shell
openssl genpkey -algorithm ed25519 -outform DER >privkey
openssl pkey -in privkey -pubout -out pubkey -inform DER -outform DER1
2
2
Convert DID controller public key to Base64URL:
shell
cat pubkey| tail -c +13| basenc -w0 --base64url1
The result can then be used as value of x in Request 2.